Check if Joomla core, components and modules have known vulnerabilities.
The scanner attempts to identify security weaknesses in the target Joomla website (core, components, modules, and templates).
It performs a remote scan without authentication, using a black-box methodology. It simulates an external attacker who tries to penetrate the target Joomla website
Use this tool to reduce the time spent on your pentesting engagements. Try it to discover Joomla vulnerabilities fast.
Check if your own installation of Joomla is updated and properly configured. Enumerate your existing Joomla components, modules, templates, and verify if they are at the latest version.
If you are a web development company, you can also show this report to your clients and prove that you have implemented the proper security measures in the Joomla website.
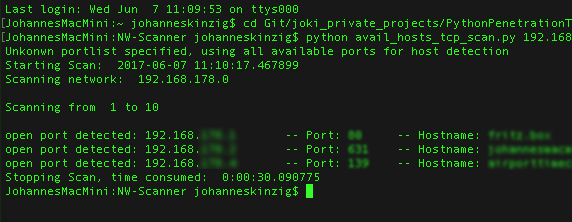
lorem ipsum lorem ipsum lorem ipsum lorem ipsum lorem ipsum lorem ipsum lorem ipsum lorem ipsum lorem ipsum lorem ipsum lorem ipsum lorem ipsum
Shows Joomla version and its known vulnerabilities
Includes the installed components, modules and templates
Gives references for vulnerability details